Blocking Ads using unbound(8) on OpenBSD
416 words, 2 minutes
The Internet is full of Ads and Trackers. Some of them are useful to monetize free content. Some are used in a non-ethical manner. Savvy users will configure Ad-Blocker on their Web browser. Others won’t. Most Appliance and IoT modules won’t allow third-party blocking addons.
Here’s how to add an extra layer of privacy using OpenBSD and its unbound(8) DNS resolver.
Pi-Hole is an OpenSource project that enables blocking Ads at the network-level. Meaning users don’t even have to care about it. What happens is that is serves as a DNS server for your LAN which simply won’t allow IP resolutions for well-known Ad services. Read the Pi-Hole documentation to learn more about it.
After reading the sources, I decided that the core feature could be implemented using OpenBSD’s stock unbound(8) and a home-made script.
The Ad blocklist
The public blocklists used by Pi-Hole are the following:
- StevenBlack
- MalwareDom
- Cameleon
- ZeusTracker
- Disconnect.me Tracking
- Disconnect.me Ads
- HostsFile
I wrote a script that will fetch the blocklists content, parse it and create a local zone file for unbound(8). That file will contain all the blocked domains and use the redirect answer to resolve those as invalid. The final unbound(8) zone file looks like this:
local-zone: "adservices.google.com" redirect
local-data: "adservices.google.com A 0.0.0.0"
(...)
local-zone: "www.doubleclick.com" redirect
local-data: "www.doubleclick.com A 0.0.0.0"
The script is regularly run from cron and the zone file is included on every unbound(8) start/reload/restart.
Configure unbound(8)
Now that the local zone file is filled with unwanted domains, using it with unbound(8) is as simple as adding the following line to unbound.conf:
# grep include /var/unbound/etc/unbound.conf
include: /var/unbound/etc/unbound-adhosts.conf
That’s all. When you look at the logs, you’ll now see things like:
logs4.xiti.com. redirect 192.168.0.26@33958 logs4.xiti.com. A IN
fls.doubleclick.net. redirect 192.168.0.26@19521 2984122.fls.doubleclick.net. A IN
googleads.g.doubleclick.net. redirect 192.168.0.26@19576 googleads.g.doubleclick.net. A IN
www.google-analytics.com. redirect 192.168.0.26@31913 www.google-analytics.com. A IN
js-agent.newrelic.com. redirect 192.168.0.26@9381 js-agent.newrelic.com. A IN
www.google-analytics.com. redirect 192.168.0.26@45277 www.google-analytics.com. A IN
www.google-analytics.com. redirect 192.168.0.26@21177 www.google-analytics.com. A IN
www.googletagmanager.com. redirect 192.168.0.26@2080 www.googletagmanager.com. A IN
ping.dozuki.com. redirect 192.168.0.26@25145 ping.dozuki.com. A IN
static.doubleclick.net. redirect 192.168.0.26@43856 static.doubleclick.net. A IN
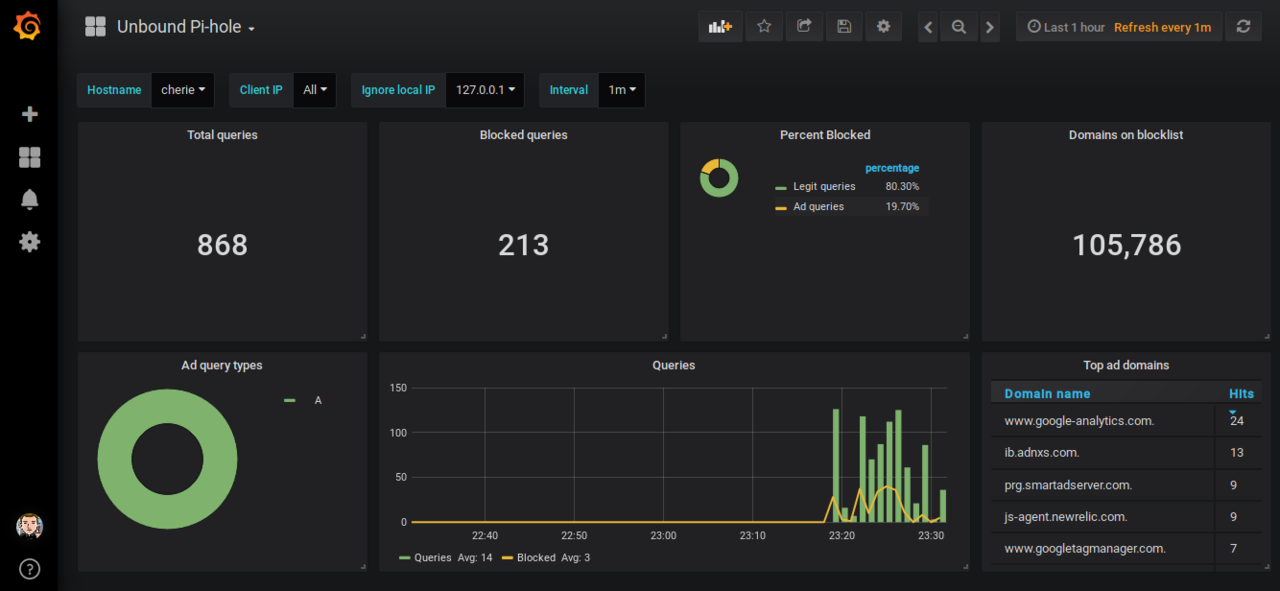
The Ad-blocker dashboard
Using syslog-ng, I parse my unbound(8) logs and store some metrics in InfluxDB. This way, it is possible to render the Ad-blocker activity using Grafana.
This is what happened when browsing sites like CNN, YouTube, TheVerge, LeMonde, LeParisien or Economie.Gouv.Fr without an AdBlocker enabled in Firefox-ESR.
I’ve been using the unbound blocklist for a month now and didn’t notice any drawbacks. Nor did I get any complains from the daughter and her smartphone…